How to do updates on the command line
Keeping your Linux computer as safe as possible from various types of cyber attacks is only possible if you perform updates regularly and upgrade to new releases when they become available. This document describes the steps you need to take to perform upgrades. I’ve written about doing upgrades so this time we’ll explore how to do updates.
Let’s start with a couple simple definitions for clarity. The terminology is often used interchangeably but I use the definitions provided here for consistency.
- Upgrades replace all or almost all packages on a Linux system thus advancing it from one release level to the next. Such as upgrading from Fedora 40 to 41.
- Updates are fixes and patches that resolve a problem or install new features and functions for individual software packages. This does not result in advancement of the release level.
Although this procedure covers updates for Fedora and other RPM-based distributions, similar tasks must be performed on other distributions as well. The details will differ, but updates must be performed on all Linux systems to maintain functionality and security.
This article covers DNF5, which is the latest version. This release has made some significant changes in DNF so be aware of that.
Preparation
Regardless of which of the following procedures you will use, you will prepare in exactly the same manner. You must use privilege escalation to obtain root capabilities. That will provide you with the administrative privileges that allow you to perform updates and upgrades. This can be done on the command line in one of two ways. You can use the su command to become root for an arbitrary amount of time until you exit from the root session. If your host is set up appropriately, you can use the sudo command to perform these tasks but which will time out after five minutes.
Becoming root
The command you type is in bold. To become root you type su, a space, and a dash ( – ). Then enter the root password. The root password is not displayed and the cursor does not move while you are typing it.
dboth@testvm1:~$ su -
Password:<Enter password>
root@testvm1:~#This method allows you to maintain root privilege as long as necessary with no worries about a timeout. You can just enter the exit command to return to your non-root session .
Using sudo
The sudo command makes it easy to escalate to root privilege, but the /etc/sudoers file must be set up correctly. That task is beyond the scope of this article. However, many modern distributions either set this up automatically for the first user created, such as Ubuntu and its derivatives, or provide the option to do so during installation, such as with Fedora.
dboth@testvm1:~$ sudo <Enter the command here>
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
For security reasons, the password you type will not be visible.
[sudo] password for dboth: <Enter the user password here>After you enter your own password — not the root password — the command will run just as if you were logged in directly as the root user. The message in the example above is typical of Red Hat and Fedora related distros and is shown only the first time the user uses the sudo command.
Whichever method you use to obtain root privilege, you’re now ready to proceed with performing updates and upgrades.
Updates
Updates are intended to ensure the current Linux release is as up to date as possible. Updates can install fixes to existing problems, minor functional enhancements, and documentation updates. Just because I use the term updates doesn’t mean that the Fedora DNF package management system does. Despite the command names in this section, we’re doing updates.
Check for updates
I suggest looking through this list for packages for the kernel, glibc, and systemd because updates to any of those packages will indicate that a reboot is required. The dnf check-update command lists all available updates from the installed and enabled repositories. DNF provides
# dnf check-update
Updating and loading repositories:
<SNIP>
Repositories loaded.
abseil-cpp.x86_64 20240722.0-2.fc41 updates
akonadi-server.x86_64 24.12.1-1.fc41 updates
akonadi-server-mysql.x86_64 24.12.1-1.fc41 updates
ark.x86_64 24.12.1-1.fc41 updates
ark-libs.x86_64 24.12.1-1.fc41 updates
audiocd-kio.x86_64 24.12.1-1.fc41 updates
<SNIP>
xfce4-terminal.x86_64 1.1.4-1.fc41 updates
xfce4-whiskermenu-plugin.x86_64 2.8.4-1.fc41 updates
xxd.x86_64 2:9.1.1000-1.fc41 updates
xxhash-libs.x86_64 0.8.3-1.fc41 updatesNow we know that there are some updates to be installed. I also like to have a list of the types of updates available, especially security ones.
# dnf updateinfo summary
Updating and loading repositories:
Repositories loaded.
Available advisory information summary:
Security : 3
Critical : 1
Important : 1
Moderate : 0
Low : 1
Other : 0
Bugfix : 24
Enhancement : 13
Other : 7Do the updates
The updates are easy.
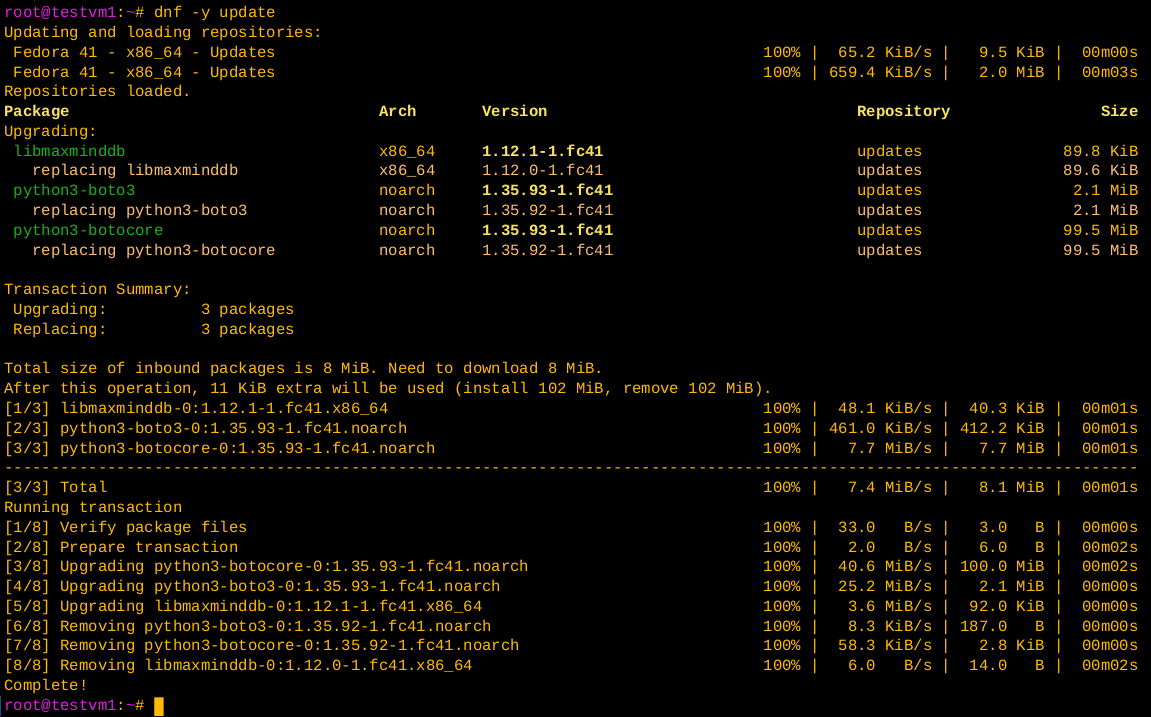
# dnf -y updateFigure 2 shows the results of performing an update on a host with only a few packages needing updates. In this case no message is displayed to indicate that a reboot is required.
Updates can take anywhere from a minute or so, up to 30 minutes or more. This depends upon the number of updates to be installed, the amount of data to be downloaded, the speed of your Internet connection, the speed of your computer, the number of CPUs, and how much memory it has — and other factors. Don’t be impatient; it will take as long as it takes.
Post-update tasks
Some additional tasks, when performed after installing updates, can be helpful. I usually perform two additional tasks.
I rebuild the man(ual) pages to ensure that all new pages are added and that obsolete ones are removed. I also update the plocate database which enables the locate command to respond quickly when you use it to locate files. You didn’t think that the locate command actually searched the entire filesystem every time you use it did you?
# mandb ; updatedbReboot if necessary
First, let’s determine whether a reboot is required. Although you can tell from some of the packages whether a reboot is needed, like the kernel and glibc, DNF provides a tool that checks to see whether a reboot is required. This tool only works after the updates are installed.
The case in Figure 2 doesn’t need a reboot, but I always check. However, to make this example more interesting, I use an updated VM that does need a reboot.
# dnf needs-restarting
Updating and loading repositories:
<SNIP>
Repositories loaded.
Core libraries or services have been updated since boot-up:
* kernel
* kernel-core
* kernel-modules
* kernel-modules-core
* kernel-modules-extra
* kernel-tools
* kernel-tools-libs
* libical
* libxcrypt
* openssl-libs
* pulseaudio-qt-qt6
* python3-perf
* systemd
Reboot is required to fully utilize these updates.
More information: https://access.redhat.com/solutions/27943In this case, 13 packages have been updated but the new versions won’t be used until the system has been rebooted. I usually reboot as soon as practical. However, I do reboot immediately in the case of critical security updates. And this is one of the things I like about Linux — we have the option of rebooting when it’s our choice. Clearly a reboot should be performed as soon as possible when it’s necessary, but that’s not always possible.
Automating updates
That is a non-trivial set of individual tasks and commands that require some decisions. Doing those tasks manually requires paying attention and some intervention to enter new commands when the previous ones complete. Because of the need to babysit while waiting to enter the next command, this takes a great deal of time to monitor each computer as it went through the procedures. There was room for error as I was reminded occasionally when I would enter the wrong command on a host.
And I usually need to do all that on the many computers in my lab and at least a few VMs.
Using the statement of requirements I created above, because that is what that first part of this article really is, it was easy to automate updates. I wrote a script that I call doUpdates.sh. It is about 500 lines in length and provides options like help, verbose mode, printing the current version number, and an option to reboot only if dnf needs-restarting indicates it does.
I use the .sh extension to the filename to indicate that the file is a shell script. That makes shell scripts easy to find using simple Linux tools.
Over half of the lines in this program are comments so I can remember how the program works the next time I need to work on it to fix a bug or add a little more function. Much of the basic function is copied from a template file that maintains all of the standard components that I use in every script I write. Because the framework for new scripts is always there, it is easy to start new ones.
You can download the doUdates.sh program from the Downloads page. The doUpdates.sh script should be located in /usr/local/bin in accordance with The Linux Filesystem Hierarchical Standard. It can be run with the command doUpdates.sh -ur in which the r option will cause it to reboot the host only if any of the conditions for that is met. Using doUpdates.sh -c checks for updates but doesn’t install them.
Be sure to use the help option ( -h ) for a description of the script and a list of options.
Summary
Installing updates is an important task for SysAdmins. Updates are issued to resolve problems, provide enhancements and, most importantly, to install security patches.
Updates need to be installed when they’re are available to be effective, rather than on an arbitrary schedule. That’s not to say that schedules are bad, but they don’t account for things like critical security or functional fixes that may be made available at any time. That does make it necessary to check to see whether updates are available and what they are.
We’ve seen that just installing updates and performing a reboot when necessary doesn’t completely finish the job. Updating the man and plocate databases is also needed.
Finally, automating this process ensures that all the necessary steps are taken every time. It also reduces the SysAdmin workload.